Data Mining. Outlier detection. Hamid Beigy. Sharif University of Technology. Fall 1395
|
|
|
- Leo Webb
- 5 years ago
- Views:
Transcription
1 Data Mining Outlier detection Hamid Beigy Sharif University of Technology Fall 1395 Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
2 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
3 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
4 Introduction Outlier detection is the process of finding data objects with behaviors that are very different from expectation. Such objects are called outliers or anomalies. An outlier is a data object that deviates significantly from the rest of the objects, as if it were generated by a different mechanism. Outlier detection and clustering analysis are two highly related tasks. Clustering finds the majority patterns in a data set and organizes the data accordingly, whereas outlier detection tries to capture those exceptional cases that deviate substantially from the majority patterns. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
5 Introduction Outliers are different from noisy data. As mentioned in Chapte dom error or variance in a measured variable. In general, noise is data analysis, including outlier detection. For example, in credit ca a customer s purchase behavior can be modeled as a random variab generate some noise transactions that may seem like random err Outlier detection is the process of finding data objects with behaviors that are very different from expectation. such as by buying a bigger lunch one day, or having one more cup o Such transactions should not be treated as outliers; otherwise, the cr would incur heavy costs from verifying that many transactions. The lose customers by bothering them with multiple false alarms. As i analysis and data mining tasks, noise should be removed before outl Outliers are interesting because they are suspected of not being gen mechanisms as the rest of the data. Therefore, in outlier detection Outliers are different from noisy data. Noise is a random error or variance in a measured variable. Outliers are interesting because they are suspected of not being generated by the same mechanisms as the rest of the data. R Figure 12.1 The objects in region R are outliers. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
6 Types of outliers the objects in region R are significantly different. It is unlikely that they follow the same distribution as the other objects in the data set. Thus, the objects in R are outliers in the data set. Outliers are different from noisy data. As mentioned in Chapter 3, noise is a random error or variance in a measured variable In general, Outliers noise and is Outlier not interesting Analysis in 547 data analysis, including outlier detection. For example, in credit card fraud detection, a customer s purchase behavior can be modeled as a random variable. A customer may generate some noise transactions that may seem like random errors or variance, Outliers can be classified into three such The as by quality buying categories: of a bigger contextual lunch one outlier day, or detection having one inmore an application cup of coffee than depends usual. on the meaningfulness Such transactionsof should the contextual not be treated attributes, as outliers; in addition otherwise, to thecredit measurement card company of the deviation wouldof incur an isheavy object costs global to the frommajority verifying in that the many space transactions. if of behavioral it The deviates company attributes. maymore also often Global outliers : A data object than lose customers not, the contextual by bothering attributes them withshould multiple befalse determined alarms. As byindomain many other experts, data which significantly from the rest ofcan analysis the be regarded and dataas mining partset. of tasks, thenoise input Global should background be removed outliers knowledge. before In many detection. are applications, neither Outliers obtaining are interesting sufficient because information they are to suspected determine of not contextual being generated attributes by the nor same collecting mechanisms as the rest of the data. Therefore, in outlier detection, it is important to sometimes called point anomalies, high-quality contextual and attribute are the data is easy. simplest type of outliers. How can we formulate meaningful contexts in contextual outlier detection? A straightforward method R simply uses group-bys of the contextual attributes as contexts. This may not be effective, however, because many group-bys may have insufficient data and/or noise. A more general method uses the proximity of data objects in the space of contextual attributes. We discuss this approach in detail in Section Collective Outliers Suppose you are a supply-chain manager of AllElectronics. You handle thousands of orders and shipments every day. If the shipment of an order is delayed, it may not be considered an outlier because, statistically, delays occur from time to time. However, you have to pay attention if 100 orders are delayed on a single day. Those 100 orders AFigure data 12.1 The objects in regionis R areaoutliers. as a whole form an outlier, although contextual each of them may outlier not be regarded if asitan outlier deviates if considered individually. You may have to take a close look at those orders collectively to understand the shipment problem. Given a data set, a subset of data objects forms a collective outlier if the objects as a whole deviate significantly from the entire data set. Importantly, the individual data objects may not be outliers. Contextual outliers : significantly with respect to a specific context of the object. For example, 0 o C is an outlier in the summer while it is not outlier in the winter. Example 12.4 Collective outliers. In Figure 12.2, the black objects as a whole form a collective outlier Collective outliers : A subset because ofthedata density those objects is much forms higher than the rest in the data set. However, every black object individually is not an outlier with respect to the whole data set. if the objects as a whole deviate significantly from the entire data set. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
7 Challenges of outlier detection Outlier detection is useful in many applications yet faces many challenges such as the following Modeling normal objects and outliers effectively : Outlier detection quality highly depends on the modeling of normal objects and outliers. Building a comprehensive model for data normality is very challenging, if not impossible. Application-specific outlier detection : Choosing the similarity/ distance measure and the relationship model to describe data objects is critical in outlier detection. Such choices are often application-dependent. Handling noise in outlier detection : Noise often unavoidably exists in data collected in many applications. Low data quality and the presence of noise bring a huge challenge to outlier detection. Understandability : A user may want to not only detect outliers, but also understand why the detected objects are outliers. amid Beigy (Sharif University of Technology) Data Mining Fall / 17
8 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
9 Outlier detection methods We can categorize outlier detection methods according to whether the sample of data for analysis is given with domain expertprovided labels that can be used to build an outlier detection model. Supervised methods : Domain experts examine and label a sample of the underlying data. Outlier detection can then be modeled as a classification problem. Unsupervised methods : Unsupervised outlier detection methods make an implicit assumption: The normal objects are somewhat clustered. In other words, an unsupervised outlier detection method expects that normal objects follow a pattern far more frequently than outliers. Semi-supervised methods : We may encounter cases where only a small set of the normal and/or outlier objects are labeled, but most of the data are unlabeled. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
10 Outlier detection methods (cont.) We can divide outlier detection methods into groups according to their assumptions regarding normal objects versus outliers. Statistical methods (model-based methods) : These methods assume that normal data objects are generated by a statistical (stochastic) model, and that data not following the model are outliers. Proximity-based methods : These methods assume that an object is an outlier if the nearest neighbors of the object are far away in feature space, that is, the proximity of the object to its neighbors significantly deviates from the proximity of most of the other objects to their neighbors in the same data set. Clustering-based methods : These methods assume that the normal data objects belong to large and dense clusters, whereas outliers belong to small or sparse clusters, or do not belong to any clusters. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
11 Statistical methods As with statistical methods for clustering, statistical methods for outlier detection make assumptions about data normality. They assume that the normal objects in a data set are generated by a stochastic process (a generative model). Consequently, normal objects occur in regions of high probability for the stochastic model, and objects in the regions of low probability are outliers. Statistical methods for outlier detection can be divided into two major categories: Parametric methods : A parametric method assumes that the normal data objects are generated by a parametric distribution with parameter θ. Nonparametric methods : A nonparametric method does not assume an a priori statistical model. Instead, a nonparametric method tries to determine the model from the input data. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
12 Statistical methods (Parametric methods) Suppose average temperature (ascending order) of a city in the last 10 years are: 24.0, 28.9, 28.9, 29.0, 29.1, 29.1, 29.2, 29.2, 29.3, and Assume that the average temperature follows a normal distribution, which is determined by two parameters: the mean, µ, and the standard deviation, σ. Using maximum likelihood estimates, we obtain ˆµ = 1 n x i = n ˆσ 2 = 1 n i=1 n (x i ˆµ) 2 = 2.29 i=1 We know that the µ ± 3σ region contains 99.7% data under the assumption of normal. The probability that value 24.0 is generated by the normal distribution is less than 0.15%, and thus can be identified as an outlier. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
13 from the input data, rather than assuming one a priori. Nonparametric methods often make fewer assumptions about the data, and thus can be applicable in more scenarios. Statistical methods (Nonparametric methods) Example Outlier detection using a histogram. AllElectronics records the purchase amount for every customer transaction. Figure 12.5 uses a histogram (refer to Chapters 2 and 3) to graph these amounts as percentages, given all transactions. For example, 60% of In nonparametric methods the transaction foramounts outlier are between detection, $0.00 and $1000. the model of normal We can use the histogram as a nonparametric statistical model to capture outliers. For data is learned from the example, input a transaction data, in therather amount of $7500 than can assuming be regarded an outlier onebecause a priori. only 1 (60% + 20% + 10% + 6.7% + 3.1%) = 0.2% of transactions have an amount Nonparametric methods higher than often $5000. make On the other fewer hand, a transaction assumptions amount of $385 about can be treated theas normal because it falls into the bin (or bucket) holding 60% of the transactions. data, and thus can be applicable more scenarios 60% 20% 0 10% 6.7% 3.1% Amount per transaction $1000 A transaction Figure in the 12.5 amount Histogram of purchase of 7500 amounts incan transactions. be regarded as an outlier because only 0.2% of transactions have an amount higher than Transaction amount of 385 can be treated as normal because it falls into the bin (or bucket) holding 60% of the transactions. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
14 Proximity-based methods In these methods, a distance measure used to quantify the similarity between objects. Objects that are far from others can be regarded as outliers. These methods assume that the proximity of an outlier object to its nearest neighbors significantly deviates from the proximity of the object to most of the other objects in the data set. There are two types of proximity-based outlier detection methods: Distance-based methods : A distance-based outlier detection method consults the neighborhood of an object, which is defined by a given radius. An object is then considered an outlier if its neighborhood does not have enough other points. Density-based methods : A density-based outlier detection method investigates the density of an object and that of its neighbors. Here, an object is identified as an outlier if its density is relatively much lower than that of its neighbors. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
15 Clustering-based methods efficiency. For example, fixed-width clustering is a linear-time tech some outlier detection methods. The idea is simple yet efficient. A a cluster if the center of the cluster is within a predefined distance point. If a point cannot be assigned to any existing cluster, a new cl distance threshold may be learned from the training data under cert Clustering-based outlier detection methods have the following ad can detect outliers without requiring any labeled data, that is, in an They work for many data types. Clusters can be regarded as sum Once the clusters are obtained, clustering-based methods need only against the clusters to determine whether the object is an outlier. Thi fast because the number of clusters is usually small compared to t The notion of outliers is highly related to that of clusters. Clustering-based approaches detect outliers by examining the relationship between objects and clusters. An outlier is an object that belongs to a small and remote cluster, or objects. does not belong to any cluster. C 3 C 1 o C 2 Figure Outliers in small clusters. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
16 Classification-based methods Outlier detection can be treated as a classification problem if a training data set with class labels is available. 72 Chapter The general 12 Outlier idea ofdetection classification-based outlier detection methods is to train a classification model that can distinguish normal data from outliers. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
17 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
18 Mining contextual outliers An object in a given data set is a contextual outlier if it deviates significantly with respect to a specific context of the object. The context is defined using contextual attributes. These depend heavily on the application, and are often provided by users as part of the contextual outlier detection task. These methods usally transform the contextual outlier detection problem into a typical outlier detection problem. Specifically, for a given data object, we can evaluate whether the object is an outlier in two steps. 1 In the first step, we identify the context of the object using the contextual attributes. 2 In the second step, we calculate the outlier score for the object in the context using a conventional outlier detection method. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
19 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
20 Mining collective outliers A group of data objects forms a collective outlier if the objects as a whole deviate significantly from the entire data set, even though each individual object in the group may not be an outlier. To detect collective outliers, we have to examine the structure of the data set, that is, the relationships between multiple data objects. The structure of the data set typically depends on the nature of the data. For outlier detection in temporal data (e.g., time series and sequences), we explore the structures formed by time, which occur in segments of the time series or sub- sequences. To detect collective outliers in spatial data, we explore local areas. In graph and network data, we explore subgraphs. Each of these structures is inherent to its respective data type. Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
21 Table of contents 1 Introduction 2 Outlier detection methods Statistical methods Proximity-based methods Clustering-based methods Classification-based methods 3 Mining contextual outliers 4 Mining collective outliers 5 Reading Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
22 Reading Read chapter 12 of the following book J. Han, M. Kamber, and Jian Pei, Data Mining: Concepts and Techniques, Morgan Kaufmann, Hamid Beigy (Sharif University of Technology) Data Mining Fall / 17
Motivation: Fraud Detection
 Outlier Detection Motivation: Fraud Detection http://i.imgur.com/ckkoaop.gif Jian Pei: CMPT 741/459 Data Mining -- Outlier Detection (1) 2 Techniques: Fraud Detection Features Dissimilarity Groups and
Outlier Detection Motivation: Fraud Detection http://i.imgur.com/ckkoaop.gif Jian Pei: CMPT 741/459 Data Mining -- Outlier Detection (1) 2 Techniques: Fraud Detection Features Dissimilarity Groups and
Class Outlier Detection. Zuzana Pekarčíková
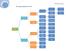
 Class Outlier Detection Zuzana Pekarčíková Outline λ What is an Outlier? λ Applications of Outlier Detection λ Types of Outliers λ Outlier Detection Methods Types λ Basic Outlier Detection Methods λ High-dimensional
Class Outlier Detection Zuzana Pekarčíková Outline λ What is an Outlier? λ Applications of Outlier Detection λ Types of Outliers λ Outlier Detection Methods Types λ Basic Outlier Detection Methods λ High-dimensional
Knowledge Discovery and Data Mining I
 Ludwig-Maximilians-Universität München Lehrstuhl für Datenbanksysteme und Data Mining Prof. Dr. Thomas Seidl Knowledge Discovery and Data Mining I Winter Semester 2018/19 Introduction What is an outlier?
Ludwig-Maximilians-Universität München Lehrstuhl für Datenbanksysteme und Data Mining Prof. Dr. Thomas Seidl Knowledge Discovery and Data Mining I Winter Semester 2018/19 Introduction What is an outlier?
Outlier Analysis. Lijun Zhang
 Outlier Analysis Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Extreme Value Analysis Probabilistic Models Clustering for Outlier Detection Distance-Based Outlier Detection Density-Based
Outlier Analysis Lijun Zhang zlj@nju.edu.cn http://cs.nju.edu.cn/zlj Outline Introduction Extreme Value Analysis Probabilistic Models Clustering for Outlier Detection Distance-Based Outlier Detection Density-Based
OUTLIER DETECTION : A REVIEW
 International Journal of Advances Outlier in Embedeed Detection System : A Review Research January-June 2011, Volume 1, Number 1, pp. 55 71 OUTLIER DETECTION : A REVIEW K. Subramanian 1, and E. Ramraj
International Journal of Advances Outlier in Embedeed Detection System : A Review Research January-June 2011, Volume 1, Number 1, pp. 55 71 OUTLIER DETECTION : A REVIEW K. Subramanian 1, and E. Ramraj
Chapter 1. Introduction
 Chapter 1 Introduction 1.1 Motivation and Goals The increasing availability and decreasing cost of high-throughput (HT) technologies coupled with the availability of computational tools and data form a
Chapter 1 Introduction 1.1 Motivation and Goals The increasing availability and decreasing cost of high-throughput (HT) technologies coupled with the availability of computational tools and data form a
T. R. Golub, D. K. Slonim & Others 1999
 T. R. Golub, D. K. Slonim & Others 1999 Big Picture in 1999 The Need for Cancer Classification Cancer classification very important for advances in cancer treatment. Cancers of Identical grade can have
T. R. Golub, D. K. Slonim & Others 1999 Big Picture in 1999 The Need for Cancer Classification Cancer classification very important for advances in cancer treatment. Cancers of Identical grade can have
Information-Theoretic Outlier Detection For Large_Scale Categorical Data
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 11 November, 2014 Page No. 9178-9182 Information-Theoretic Outlier Detection For Large_Scale Categorical
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 11 November, 2014 Page No. 9178-9182 Information-Theoretic Outlier Detection For Large_Scale Categorical
Brain Tumour Detection of MR Image Using Naïve Beyer classifier and Support Vector Machine
 International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume 3 Issue 3 ISSN : 2456-3307 Brain Tumour Detection of MR Image Using Naïve
International Journal of Scientific Research in Computer Science, Engineering and Information Technology 2018 IJSRCSEIT Volume 3 Issue 3 ISSN : 2456-3307 Brain Tumour Detection of MR Image Using Naïve
Gene expression analysis. Roadmap. Microarray technology: how it work Applications: what can we do with it Preprocessing: Classification Clustering
 Gene expression analysis Roadmap Microarray technology: how it work Applications: what can we do with it Preprocessing: Image processing Data normalization Classification Clustering Biclustering 1 Gene
Gene expression analysis Roadmap Microarray technology: how it work Applications: what can we do with it Preprocessing: Image processing Data normalization Classification Clustering Biclustering 1 Gene
CSE 258 Lecture 1.5. Web Mining and Recommender Systems. Supervised learning Regression
 CSE 258 Lecture 1.5 Web Mining and Recommender Systems Supervised learning Regression What is supervised learning? Supervised learning is the process of trying to infer from labeled data the underlying
CSE 258 Lecture 1.5 Web Mining and Recommender Systems Supervised learning Regression What is supervised learning? Supervised learning is the process of trying to infer from labeled data the underlying
Proceedings of the UGC Sponsored National Conference on Advanced Networking and Applications, 27 th March 2015
 Brain Tumor Detection and Identification Using K-Means Clustering Technique Malathi R Department of Computer Science, SAAS College, Ramanathapuram, Email: malapraba@gmail.com Dr. Nadirabanu Kamal A R Department
Brain Tumor Detection and Identification Using K-Means Clustering Technique Malathi R Department of Computer Science, SAAS College, Ramanathapuram, Email: malapraba@gmail.com Dr. Nadirabanu Kamal A R Department
Using Bayesian Networks to Analyze Expression Data. Xu Siwei, s Muhammad Ali Faisal, s Tejal Joshi, s
 Using Bayesian Networks to Analyze Expression Data Xu Siwei, s0789023 Muhammad Ali Faisal, s0677834 Tejal Joshi, s0677858 Outline Introduction Bayesian Networks Equivalence Classes Applying to Expression
Using Bayesian Networks to Analyze Expression Data Xu Siwei, s0789023 Muhammad Ali Faisal, s0677834 Tejal Joshi, s0677858 Outline Introduction Bayesian Networks Equivalence Classes Applying to Expression
Hierarchical Bayesian Modeling of Individual Differences in Texture Discrimination
 Hierarchical Bayesian Modeling of Individual Differences in Texture Discrimination Timothy N. Rubin (trubin@uci.edu) Michael D. Lee (mdlee@uci.edu) Charles F. Chubb (cchubb@uci.edu) Department of Cognitive
Hierarchical Bayesian Modeling of Individual Differences in Texture Discrimination Timothy N. Rubin (trubin@uci.edu) Michael D. Lee (mdlee@uci.edu) Charles F. Chubb (cchubb@uci.edu) Department of Cognitive
ASSIGNMENT 2. Question 4.1 In each of the following situations, describe a sample space S for the random phenomenon.
 ASSIGNMENT 2 MGCR 271 SUMMER 2009 - DUE THURSDAY, MAY 21, 2009 AT 18:05 IN CLASS Question 4.1 In each of the following situations, describe a sample space S for the random phenomenon. (1) A new business
ASSIGNMENT 2 MGCR 271 SUMMER 2009 - DUE THURSDAY, MAY 21, 2009 AT 18:05 IN CLASS Question 4.1 In each of the following situations, describe a sample space S for the random phenomenon. (1) A new business
Inferring Social Structure of Animal Groups From Tracking Data
 Inferring Social Structure of Animal Groups From Tracking Data Brian Hrolenok 1, Hanuma Teja Maddali 1, Michael Novitzky 1, Tucker Balch 1 and Kim Wallen 2 1 Georgia Institute of Technology, Atlanta, GA
Inferring Social Structure of Animal Groups From Tracking Data Brian Hrolenok 1, Hanuma Teja Maddali 1, Michael Novitzky 1, Tucker Balch 1 and Kim Wallen 2 1 Georgia Institute of Technology, Atlanta, GA
SURVEY ON OUTLIER DETECTION TECHNIQUES USING CATEGORICAL DATA
 SURVEY ON OUTLIER DETECTION TECHNIQUES USING CATEGORICAL DATA K.T.Divya 1, N.Senthil Kumaran 2 1Research Scholar, Department of Computer Science, Vellalar college for Women, Erode, Tamilnadu, India 2Assistant
SURVEY ON OUTLIER DETECTION TECHNIQUES USING CATEGORICAL DATA K.T.Divya 1, N.Senthil Kumaran 2 1Research Scholar, Department of Computer Science, Vellalar college for Women, Erode, Tamilnadu, India 2Assistant
For general queries, contact
 Much of the work in Bayesian econometrics has focused on showing the value of Bayesian methods for parametric models (see, for example, Geweke (2005), Koop (2003), Li and Tobias (2011), and Rossi, Allenby,
Much of the work in Bayesian econometrics has focused on showing the value of Bayesian methods for parametric models (see, for example, Geweke (2005), Koop (2003), Li and Tobias (2011), and Rossi, Allenby,
RAG Rating Indicator Values
 Technical Guide RAG Rating Indicator Values Introduction This document sets out Public Health England s standard approach to the use of RAG ratings for indicator values in relation to comparator or benchmark
Technical Guide RAG Rating Indicator Values Introduction This document sets out Public Health England s standard approach to the use of RAG ratings for indicator values in relation to comparator or benchmark
A NOVEL VARIABLE SELECTION METHOD BASED ON FREQUENT PATTERN TREE FOR REAL-TIME TRAFFIC ACCIDENT RISK PREDICTION
 OPT-i An International Conference on Engineering and Applied Sciences Optimization M. Papadrakakis, M.G. Karlaftis, N.D. Lagaros (eds.) Kos Island, Greece, 4-6 June 2014 A NOVEL VARIABLE SELECTION METHOD
OPT-i An International Conference on Engineering and Applied Sciences Optimization M. Papadrakakis, M.G. Karlaftis, N.D. Lagaros (eds.) Kos Island, Greece, 4-6 June 2014 A NOVEL VARIABLE SELECTION METHOD
Outlier Detection Based on Surfeit Entropy for Large Scale Categorical Data Set
 Outlier Detection Based on Surfeit Entropy for Large Scale Categorical Data Set Neha L. Bagal PVPIT, Bavdhan, Pune, Savitribai Phule Pune University, India Abstract: Number of methods on classification,
Outlier Detection Based on Surfeit Entropy for Large Scale Categorical Data Set Neha L. Bagal PVPIT, Bavdhan, Pune, Savitribai Phule Pune University, India Abstract: Number of methods on classification,
Bayesian and Frequentist Approaches
 Bayesian and Frequentist Approaches G. Jogesh Babu Penn State University http://sites.stat.psu.edu/ babu http://astrostatistics.psu.edu All models are wrong But some are useful George E. P. Box (son-in-law
Bayesian and Frequentist Approaches G. Jogesh Babu Penn State University http://sites.stat.psu.edu/ babu http://astrostatistics.psu.edu All models are wrong But some are useful George E. P. Box (son-in-law
What you should know before you collect data. BAE 815 (Fall 2017) Dr. Zifei Liu
 What you should know before you collect data BAE 815 (Fall 2017) Dr. Zifei Liu Zifeiliu@ksu.edu Types and levels of study Descriptive statistics Inferential statistics How to choose a statistical test
What you should know before you collect data BAE 815 (Fall 2017) Dr. Zifei Liu Zifeiliu@ksu.edu Types and levels of study Descriptive statistics Inferential statistics How to choose a statistical test
UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Midterm, 2016
 UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Midterm, 2016 Exam policy: This exam allows one one-page, two-sided cheat sheet; No other materials. Time: 80 minutes. Be sure to write your name and
UNIVERSITY of PENNSYLVANIA CIS 520: Machine Learning Midterm, 2016 Exam policy: This exam allows one one-page, two-sided cheat sheet; No other materials. Time: 80 minutes. Be sure to write your name and
1.4 - Linear Regression and MS Excel
 1.4 - Linear Regression and MS Excel Regression is an analytic technique for determining the relationship between a dependent variable and an independent variable. When the two variables have a linear
1.4 - Linear Regression and MS Excel Regression is an analytic technique for determining the relationship between a dependent variable and an independent variable. When the two variables have a linear
Mining Dynamic Relationships From Spatio-temporal Datasets: An Application to Brain fmri Data
 Mining Dynamic Relationships From Spatio-temporal Datasets: An Application to Brain fmri Data A THESIS SUBMITTED TO THE FACULTY OF THE GRADUATE SCHOOL OF THE UNIVERSITY OF MINNESOTA BY Gowtham Atluri IN
Mining Dynamic Relationships From Spatio-temporal Datasets: An Application to Brain fmri Data A THESIS SUBMITTED TO THE FACULTY OF THE GRADUATE SCHOOL OF THE UNIVERSITY OF MINNESOTA BY Gowtham Atluri IN
Lecture #4: Overabundance Analysis and Class Discovery
 236632 Topics in Microarray Data nalysis Winter 2004-5 November 15, 2004 Lecture #4: Overabundance nalysis and Class Discovery Lecturer: Doron Lipson Scribes: Itai Sharon & Tomer Shiran 1 Differentially
236632 Topics in Microarray Data nalysis Winter 2004-5 November 15, 2004 Lecture #4: Overabundance nalysis and Class Discovery Lecturer: Doron Lipson Scribes: Itai Sharon & Tomer Shiran 1 Differentially
Choosing a Significance Test. Student Resource Sheet
 Choosing a Significance Test Student Resource Sheet Choosing Your Test Choosing an appropriate type of significance test is a very important consideration in analyzing data. If an inappropriate test is
Choosing a Significance Test Student Resource Sheet Choosing Your Test Choosing an appropriate type of significance test is a very important consideration in analyzing data. If an inappropriate test is
Variability. After reading this chapter, you should be able to do the following:
 LEARIG OBJECTIVES C H A P T E R 3 Variability After reading this chapter, you should be able to do the following: Explain what the standard deviation measures Compute the variance and the standard deviation
LEARIG OBJECTIVES C H A P T E R 3 Variability After reading this chapter, you should be able to do the following: Explain what the standard deviation measures Compute the variance and the standard deviation
extraction can take place. Another problem is that the treatment for chronic diseases is sequential based upon the progression of the disease.
 ix Preface The purpose of this text is to show how the investigation of healthcare databases can be used to examine physician decisions to develop evidence-based treatment guidelines that optimize patient
ix Preface The purpose of this text is to show how the investigation of healthcare databases can be used to examine physician decisions to develop evidence-based treatment guidelines that optimize patient
A STATISTICAL PATTERN RECOGNITION PARADIGM FOR VIBRATION-BASED STRUCTURAL HEALTH MONITORING
 A STATISTICAL PATTERN RECOGNITION PARADIGM FOR VIBRATION-BASED STRUCTURAL HEALTH MONITORING HOON SOHN Postdoctoral Research Fellow ESA-EA, MS C96 Los Alamos National Laboratory Los Alamos, NM 87545 CHARLES
A STATISTICAL PATTERN RECOGNITION PARADIGM FOR VIBRATION-BASED STRUCTURAL HEALTH MONITORING HOON SOHN Postdoctoral Research Fellow ESA-EA, MS C96 Los Alamos National Laboratory Los Alamos, NM 87545 CHARLES
A Comparison of Collaborative Filtering Methods for Medication Reconciliation
 A Comparison of Collaborative Filtering Methods for Medication Reconciliation Huanian Zheng, Rema Padman, Daniel B. Neill The H. John Heinz III College, Carnegie Mellon University, Pittsburgh, PA, 15213,
A Comparison of Collaborative Filtering Methods for Medication Reconciliation Huanian Zheng, Rema Padman, Daniel B. Neill The H. John Heinz III College, Carnegie Mellon University, Pittsburgh, PA, 15213,
Chapter 11. Experimental Design: One-Way Independent Samples Design
 11-1 Chapter 11. Experimental Design: One-Way Independent Samples Design Advantages and Limitations Comparing Two Groups Comparing t Test to ANOVA Independent Samples t Test Independent Samples ANOVA Comparing
11-1 Chapter 11. Experimental Design: One-Way Independent Samples Design Advantages and Limitations Comparing Two Groups Comparing t Test to ANOVA Independent Samples t Test Independent Samples ANOVA Comparing
TITLE: A Data-Driven Approach to Patient Risk Stratification for Acute Respiratory Distress Syndrome (ARDS)
 TITLE: A Data-Driven Approach to Patient Risk Stratification for Acute Respiratory Distress Syndrome (ARDS) AUTHORS: Tejas Prahlad INTRODUCTION Acute Respiratory Distress Syndrome (ARDS) is a condition
TITLE: A Data-Driven Approach to Patient Risk Stratification for Acute Respiratory Distress Syndrome (ARDS) AUTHORS: Tejas Prahlad INTRODUCTION Acute Respiratory Distress Syndrome (ARDS) is a condition
Unit 1 Exploring and Understanding Data
 Unit 1 Exploring and Understanding Data Area Principle Bar Chart Boxplot Conditional Distribution Dotplot Empirical Rule Five Number Summary Frequency Distribution Frequency Polygon Histogram Interquartile
Unit 1 Exploring and Understanding Data Area Principle Bar Chart Boxplot Conditional Distribution Dotplot Empirical Rule Five Number Summary Frequency Distribution Frequency Polygon Histogram Interquartile
Lecture II: Difference in Difference and Regression Discontinuity
 Review Lecture II: Difference in Difference and Regression Discontinuity it From Lecture I Causality is difficult to Show from cross sectional observational studies What caused what? X caused Y, Y caused
Review Lecture II: Difference in Difference and Regression Discontinuity it From Lecture I Causality is difficult to Show from cross sectional observational studies What caused what? X caused Y, Y caused
Measuring Focused Attention Using Fixation Inner-Density
 Measuring Focused Attention Using Fixation Inner-Density Wen Liu, Mina Shojaeizadeh, Soussan Djamasbi, Andrew C. Trapp User Experience & Decision Making Research Laboratory, Worcester Polytechnic Institute
Measuring Focused Attention Using Fixation Inner-Density Wen Liu, Mina Shojaeizadeh, Soussan Djamasbi, Andrew C. Trapp User Experience & Decision Making Research Laboratory, Worcester Polytechnic Institute
Lecture Notes Module 2
 Lecture Notes Module 2 Two-group Experimental Designs The goal of most research is to assess a possible causal relation between the response variable and another variable called the independent variable.
Lecture Notes Module 2 Two-group Experimental Designs The goal of most research is to assess a possible causal relation between the response variable and another variable called the independent variable.
COMPARATIVE STUDY ON FEATURE EXTRACTION METHOD FOR BREAST CANCER CLASSIFICATION
 COMPARATIVE STUDY ON FEATURE EXTRACTION METHOD FOR BREAST CANCER CLASSIFICATION 1 R.NITHYA, 2 B.SANTHI 1 Asstt Prof., School of Computing, SASTRA University, Thanjavur, Tamilnadu, India-613402 2 Prof.,
COMPARATIVE STUDY ON FEATURE EXTRACTION METHOD FOR BREAST CANCER CLASSIFICATION 1 R.NITHYA, 2 B.SANTHI 1 Asstt Prof., School of Computing, SASTRA University, Thanjavur, Tamilnadu, India-613402 2 Prof.,
FUNNEL: Automatic Mining of Spatially Coevolving Epidemics
 FUNNEL: Automatic Mining of Spatially Coevolving Epidemics By Yasuo Matsubara, Yasushi Sakurai, Willem G. van Panhuis, and Christos Faloutsos SIGKDD 2014 Presented by Sarunya Pumma This presentation has
FUNNEL: Automatic Mining of Spatially Coevolving Epidemics By Yasuo Matsubara, Yasushi Sakurai, Willem G. van Panhuis, and Christos Faloutsos SIGKDD 2014 Presented by Sarunya Pumma This presentation has
From Biostatistics Using JMP: A Practical Guide. Full book available for purchase here. Chapter 1: Introduction... 1
 From Biostatistics Using JMP: A Practical Guide. Full book available for purchase here. Contents Dedication... iii Acknowledgments... xi About This Book... xiii About the Author... xvii Chapter 1: Introduction...
From Biostatistics Using JMP: A Practical Guide. Full book available for purchase here. Contents Dedication... iii Acknowledgments... xi About This Book... xiii About the Author... xvii Chapter 1: Introduction...
Introduction to Discrimination in Microarray Data Analysis
 Introduction to Discrimination in Microarray Data Analysis Jane Fridlyand CBMB University of California, San Francisco Genentech Hall Auditorium, Mission Bay, UCSF October 23, 2004 1 Case Study: Van t
Introduction to Discrimination in Microarray Data Analysis Jane Fridlyand CBMB University of California, San Francisco Genentech Hall Auditorium, Mission Bay, UCSF October 23, 2004 1 Case Study: Van t
C-1: Variables which are measured on a continuous scale are described in terms of three key characteristics central tendency, variability, and shape.
 MODULE 02: DESCRIBING DT SECTION C: KEY POINTS C-1: Variables which are measured on a continuous scale are described in terms of three key characteristics central tendency, variability, and shape. C-2:
MODULE 02: DESCRIBING DT SECTION C: KEY POINTS C-1: Variables which are measured on a continuous scale are described in terms of three key characteristics central tendency, variability, and shape. C-2:
Automatic Hemorrhage Classification System Based On Svm Classifier
 Automatic Hemorrhage Classification System Based On Svm Classifier Abstract - Brain hemorrhage is a bleeding in or around the brain which are caused by head trauma, high blood pressure and intracranial
Automatic Hemorrhage Classification System Based On Svm Classifier Abstract - Brain hemorrhage is a bleeding in or around the brain which are caused by head trauma, high blood pressure and intracranial
Application of Local Control Strategy in analyses of the effects of Radon on Lung Cancer Mortality for 2,881 US Counties
 Application of Local Control Strategy in analyses of the effects of Radon on Lung Cancer Mortality for 2,881 US Counties Bob Obenchain, Risk Benefit Statistics, August 2015 Our motivation for using a Cut-Point
Application of Local Control Strategy in analyses of the effects of Radon on Lung Cancer Mortality for 2,881 US Counties Bob Obenchain, Risk Benefit Statistics, August 2015 Our motivation for using a Cut-Point
Conditional Distributions and the Bivariate Normal Distribution. James H. Steiger
 Conditional Distributions and the Bivariate Normal Distribution James H. Steiger Overview In this module, we have several goals: Introduce several technical terms Bivariate frequency distribution Marginal
Conditional Distributions and the Bivariate Normal Distribution James H. Steiger Overview In this module, we have several goals: Introduce several technical terms Bivariate frequency distribution Marginal
Data and Statistics 101: Key Concepts in the Collection, Analysis, and Application of Child Welfare Data
 TECHNICAL REPORT Data and Statistics 101: Key Concepts in the Collection, Analysis, and Application of Child Welfare Data CONTENTS Executive Summary...1 Introduction...2 Overview of Data Analysis Concepts...2
TECHNICAL REPORT Data and Statistics 101: Key Concepts in the Collection, Analysis, and Application of Child Welfare Data CONTENTS Executive Summary...1 Introduction...2 Overview of Data Analysis Concepts...2
CHAPTER 6 HUMAN BEHAVIOR UNDERSTANDING MODEL
 127 CHAPTER 6 HUMAN BEHAVIOR UNDERSTANDING MODEL 6.1 INTRODUCTION Analyzing the human behavior in video sequences is an active field of research for the past few years. The vital applications of this field
127 CHAPTER 6 HUMAN BEHAVIOR UNDERSTANDING MODEL 6.1 INTRODUCTION Analyzing the human behavior in video sequences is an active field of research for the past few years. The vital applications of this field
EXTRACT THE BREAST CANCER IN MAMMOGRAM IMAGES
 International Journal of Civil Engineering and Technology (IJCIET) Volume 10, Issue 02, February 2019, pp. 96-105, Article ID: IJCIET_10_02_012 Available online at http://www.iaeme.com/ijciet/issues.asp?jtype=ijciet&vtype=10&itype=02
International Journal of Civil Engineering and Technology (IJCIET) Volume 10, Issue 02, February 2019, pp. 96-105, Article ID: IJCIET_10_02_012 Available online at http://www.iaeme.com/ijciet/issues.asp?jtype=ijciet&vtype=10&itype=02
The Outlier Approach How To Triumph In Your Career As A Nonconformist
 The Outlier Approach How To Triumph In Your Career As A Nonconformist We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing it on
The Outlier Approach How To Triumph In Your Career As A Nonconformist We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing it on
Comparative study of Naïve Bayes Classifier and KNN for Tuberculosis
 Comparative study of Naïve Bayes Classifier and KNN for Tuberculosis Hardik Maniya Mosin I. Hasan Komal P. Patel ABSTRACT Data mining is applied in medical field since long back to predict disease like
Comparative study of Naïve Bayes Classifier and KNN for Tuberculosis Hardik Maniya Mosin I. Hasan Komal P. Patel ABSTRACT Data mining is applied in medical field since long back to predict disease like
Hacettepe University Department of Computer Science & Engineering
 Subject Hacettepe University Department of Computer Science & Engineering Submission Date : 29 May 2013 Deadline : 12 Jun 2013 Language/version Advisor BBM 204 SOFTWARE LABORATORY II EXPERIMENT 5 for section
Subject Hacettepe University Department of Computer Science & Engineering Submission Date : 29 May 2013 Deadline : 12 Jun 2013 Language/version Advisor BBM 204 SOFTWARE LABORATORY II EXPERIMENT 5 for section
Predicting Breast Cancer Survival Using Treatment and Patient Factors
 Predicting Breast Cancer Survival Using Treatment and Patient Factors William Chen wchen808@stanford.edu Henry Wang hwang9@stanford.edu 1. Introduction Breast cancer is the leading type of cancer in women
Predicting Breast Cancer Survival Using Treatment and Patient Factors William Chen wchen808@stanford.edu Henry Wang hwang9@stanford.edu 1. Introduction Breast cancer is the leading type of cancer in women
10CS664: PATTERN RECOGNITION QUESTION BANK
 10CS664: PATTERN RECOGNITION QUESTION BANK Assignments would be handed out in class as well as posted on the class blog for the course. Please solve the problems in the exercises of the prescribed text
10CS664: PATTERN RECOGNITION QUESTION BANK Assignments would be handed out in class as well as posted on the class blog for the course. Please solve the problems in the exercises of the prescribed text
Framework for Comparative Research on Relational Information Displays
 Framework for Comparative Research on Relational Information Displays Sung Park and Richard Catrambone 2 School of Psychology & Graphics, Visualization, and Usability Center (GVU) Georgia Institute of
Framework for Comparative Research on Relational Information Displays Sung Park and Richard Catrambone 2 School of Psychology & Graphics, Visualization, and Usability Center (GVU) Georgia Institute of
NeuroMem. RBF Decision Space Mapping
 NeuroMem RBF Decision Space Mapping Version 4.2 Revised 01/04/2017 This manual is copyrighted and published by General Vision Inc. All rights reserved. Contents 1 Introduction to a decision space... 3
NeuroMem RBF Decision Space Mapping Version 4.2 Revised 01/04/2017 This manual is copyrighted and published by General Vision Inc. All rights reserved. Contents 1 Introduction to a decision space... 3
STAT445 Midterm Project1
 STAT445 Midterm Project1 Executive Summary This report works on the dataset of Part of This Nutritious Breakfast! In this dataset, 77 different breakfast cereals were collected. The dataset also explores
STAT445 Midterm Project1 Executive Summary This report works on the dataset of Part of This Nutritious Breakfast! In this dataset, 77 different breakfast cereals were collected. The dataset also explores
Improved Intelligent Classification Technique Based On Support Vector Machines
 Improved Intelligent Classification Technique Based On Support Vector Machines V.Vani Asst.Professor,Department of Computer Science,JJ College of Arts and Science,Pudukkottai. Abstract:An abnormal growth
Improved Intelligent Classification Technique Based On Support Vector Machines V.Vani Asst.Professor,Department of Computer Science,JJ College of Arts and Science,Pudukkottai. Abstract:An abnormal growth
Chapter 1: Exploring Data
 Chapter 1: Exploring Data Key Vocabulary:! individual! variable! frequency table! relative frequency table! distribution! pie chart! bar graph! two-way table! marginal distributions! conditional distributions!
Chapter 1: Exploring Data Key Vocabulary:! individual! variable! frequency table! relative frequency table! distribution! pie chart! bar graph! two-way table! marginal distributions! conditional distributions!
Evaluation on liver fibrosis stages using the k-means clustering algorithm
 Annals of University of Craiova, Math. Comp. Sci. Ser. Volume 36(2), 2009, Pages 19 24 ISSN: 1223-6934 Evaluation on liver fibrosis stages using the k-means clustering algorithm Marina Gorunescu, Florin
Annals of University of Craiova, Math. Comp. Sci. Ser. Volume 36(2), 2009, Pages 19 24 ISSN: 1223-6934 Evaluation on liver fibrosis stages using the k-means clustering algorithm Marina Gorunescu, Florin
Dmitriy Fradkin. Ask.com
 Using cluster analysis to determine the influence of demographic features on medical status of lung cancer patients Dmitriy Fradkin Askcom dmitriyfradkin@askcom Joint work with Dona Schneider (Bloustein
Using cluster analysis to determine the influence of demographic features on medical status of lung cancer patients Dmitriy Fradkin Askcom dmitriyfradkin@askcom Joint work with Dona Schneider (Bloustein
CHAPTER 3 DATA ANALYSIS: DESCRIBING DATA
 Data Analysis: Describing Data CHAPTER 3 DATA ANALYSIS: DESCRIBING DATA In the analysis process, the researcher tries to evaluate the data collected both from written documents and from other sources such
Data Analysis: Describing Data CHAPTER 3 DATA ANALYSIS: DESCRIBING DATA In the analysis process, the researcher tries to evaluate the data collected both from written documents and from other sources such
Research Article Detection of Abnormal Item Based on Time Intervals for Recommender Systems
 e Scientific World Journal, Article ID 845897, 8 pages http://dx.doi.org/0.55/204/845897 Research Article Detection of Abnormal Item Based on Time Intervals for Recommender Systems Min Gao,,2 Quan Yuan,
e Scientific World Journal, Article ID 845897, 8 pages http://dx.doi.org/0.55/204/845897 Research Article Detection of Abnormal Item Based on Time Intervals for Recommender Systems Min Gao,,2 Quan Yuan,
Practice First Midterm Exam
 Practice First Midterm Exam Statistics 200 (Pfenning) This is a closed book exam worth 150 points. You are allowed to use a calculator and a two-sided sheet of notes. There are 9 problems, with point values
Practice First Midterm Exam Statistics 200 (Pfenning) This is a closed book exam worth 150 points. You are allowed to use a calculator and a two-sided sheet of notes. There are 9 problems, with point values
Ecological Statistics
 A Primer of Ecological Statistics Second Edition Nicholas J. Gotelli University of Vermont Aaron M. Ellison Harvard Forest Sinauer Associates, Inc. Publishers Sunderland, Massachusetts U.S.A. Brief Contents
A Primer of Ecological Statistics Second Edition Nicholas J. Gotelli University of Vermont Aaron M. Ellison Harvard Forest Sinauer Associates, Inc. Publishers Sunderland, Massachusetts U.S.A. Brief Contents
Type II Fuzzy Possibilistic C-Mean Clustering
 IFSA-EUSFLAT Type II Fuzzy Possibilistic C-Mean Clustering M.H. Fazel Zarandi, M. Zarinbal, I.B. Turksen, Department of Industrial Engineering, Amirkabir University of Technology, P.O. Box -, Tehran, Iran
IFSA-EUSFLAT Type II Fuzzy Possibilistic C-Mean Clustering M.H. Fazel Zarandi, M. Zarinbal, I.B. Turksen, Department of Industrial Engineering, Amirkabir University of Technology, P.O. Box -, Tehran, Iran
Chapter Three in-class Exercises. MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question.
 Name Chapter Three in-class Exercises MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) The table below lists the populations, in thousands, of several
Name Chapter Three in-class Exercises MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) The table below lists the populations, in thousands, of several
Conditional Outlier Detection for Clinical Alerting
 Conditional Outlier Detection for Clinical Alerting Milos Hauskrecht, PhD 1, Michal Valko, MSc 1, Iyad Batal, MSc 1, Gilles Clermont, MD, MS 2, Shyam Visweswaran MD, PhD 3, Gregory F. Cooper, MD, PhD 3
Conditional Outlier Detection for Clinical Alerting Milos Hauskrecht, PhD 1, Michal Valko, MSc 1, Iyad Batal, MSc 1, Gilles Clermont, MD, MS 2, Shyam Visweswaran MD, PhD 3, Gregory F. Cooper, MD, PhD 3
Fixed-Effect Versus Random-Effects Models
 PART 3 Fixed-Effect Versus Random-Effects Models Introduction to Meta-Analysis. Michael Borenstein, L. V. Hedges, J. P. T. Higgins and H. R. Rothstein 2009 John Wiley & Sons, Ltd. ISBN: 978-0-470-05724-7
PART 3 Fixed-Effect Versus Random-Effects Models Introduction to Meta-Analysis. Michael Borenstein, L. V. Hedges, J. P. T. Higgins and H. R. Rothstein 2009 John Wiley & Sons, Ltd. ISBN: 978-0-470-05724-7
STAT100 Module 4. Detecting abnormalities. Dr. Matias Salibian-Barrera Winter 2009 / 2010
 STAT100 Module 4 Detecting abnormalities Dr. Matias Salibian-Barrera Winter 2009 / 2010 Contact information matias@stat.ubc.ca Subject: STAT100 Subject: Hi Subject: Subject: Question LSK 327 604 822 3410
STAT100 Module 4 Detecting abnormalities Dr. Matias Salibian-Barrera Winter 2009 / 2010 Contact information matias@stat.ubc.ca Subject: STAT100 Subject: Hi Subject: Subject: Question LSK 327 604 822 3410
FORECASTING TRENDS FOR PROACTIVE CRIME PREVENTION AND DETECTION USING WEKA DATA MINING TOOL-KIT ABSTRACT
 FORECASTING TRENDS FOR PROACTIVE CRIME PREVENTION AND DETECTION USING WEKA DATA MINING TOOL-KIT Ramesh Singh National Informatics Centre, New Delhi, India Rahul Thukral Department Of Computer Science And
FORECASTING TRENDS FOR PROACTIVE CRIME PREVENTION AND DETECTION USING WEKA DATA MINING TOOL-KIT Ramesh Singh National Informatics Centre, New Delhi, India Rahul Thukral Department Of Computer Science And
Psychology 205, Revelle, Fall 2014 Research Methods in Psychology Mid-Term. Name:
 Name: 1. (2 points) What is the primary advantage of using the median instead of the mean as a measure of central tendency? It is less affected by outliers. 2. (2 points) Why is counterbalancing important
Name: 1. (2 points) What is the primary advantage of using the median instead of the mean as a measure of central tendency? It is less affected by outliers. 2. (2 points) Why is counterbalancing important
Technical Specifications
 Technical Specifications In order to provide summary information across a set of exercises, all tests must employ some form of scoring models. The most familiar of these scoring models is the one typically
Technical Specifications In order to provide summary information across a set of exercises, all tests must employ some form of scoring models. The most familiar of these scoring models is the one typically
Chapter 1: Introduction to Statistics
 Chapter 1: Introduction to Statistics Variables A variable is a characteristic or condition that can change or take on different values. Most research begins with a general question about the relationship
Chapter 1: Introduction to Statistics Variables A variable is a characteristic or condition that can change or take on different values. Most research begins with a general question about the relationship
EXERCISE: HOW TO DO POWER CALCULATIONS IN OPTIMAL DESIGN SOFTWARE
 ...... EXERCISE: HOW TO DO POWER CALCULATIONS IN OPTIMAL DESIGN SOFTWARE TABLE OF CONTENTS 73TKey Vocabulary37T... 1 73TIntroduction37T... 73TUsing the Optimal Design Software37T... 73TEstimating Sample
...... EXERCISE: HOW TO DO POWER CALCULATIONS IN OPTIMAL DESIGN SOFTWARE TABLE OF CONTENTS 73TKey Vocabulary37T... 1 73TIntroduction37T... 73TUsing the Optimal Design Software37T... 73TEstimating Sample
Changing expectations about speed alters perceived motion direction
 Current Biology, in press Supplemental Information: Changing expectations about speed alters perceived motion direction Grigorios Sotiropoulos, Aaron R. Seitz, and Peggy Seriès Supplemental Data Detailed
Current Biology, in press Supplemental Information: Changing expectations about speed alters perceived motion direction Grigorios Sotiropoulos, Aaron R. Seitz, and Peggy Seriès Supplemental Data Detailed
Research Methods in Forest Sciences: Learning Diary. Yoko Lu December Research process
 Research Methods in Forest Sciences: Learning Diary Yoko Lu 285122 9 December 2016 1. Research process It is important to pursue and apply knowledge and understand the world under both natural and social
Research Methods in Forest Sciences: Learning Diary Yoko Lu 285122 9 December 2016 1. Research process It is important to pursue and apply knowledge and understand the world under both natural and social
Research Methods 1 Handouts, Graham Hole,COGS - version 1.0, September 2000: Page 1:
 Research Methods 1 Handouts, Graham Hole,COGS - version 10, September 000: Page 1: T-TESTS: When to use a t-test: The simplest experimental design is to have two conditions: an "experimental" condition
Research Methods 1 Handouts, Graham Hole,COGS - version 10, September 000: Page 1: T-TESTS: When to use a t-test: The simplest experimental design is to have two conditions: an "experimental" condition
COST EFFECTIVENESS STATISTIC: A PROPOSAL TO TAKE INTO ACCOUNT THE PATIENT STRATIFICATION FACTORS. C. D'Urso, IEEE senior member
 COST EFFECTIVENESS STATISTIC: A PROPOSAL TO TAKE INTO ACCOUNT THE PATIENT STRATIFICATION FACTORS ABSTRACT C. D'Urso, IEEE senior member The solution here proposed can be used to conduct economic analysis
COST EFFECTIVENESS STATISTIC: A PROPOSAL TO TAKE INTO ACCOUNT THE PATIENT STRATIFICATION FACTORS ABSTRACT C. D'Urso, IEEE senior member The solution here proposed can be used to conduct economic analysis
Information Processing During Transient Responses in the Crayfish Visual System
 Information Processing During Transient Responses in the Crayfish Visual System Christopher J. Rozell, Don. H. Johnson and Raymon M. Glantz Department of Electrical & Computer Engineering Department of
Information Processing During Transient Responses in the Crayfish Visual System Christopher J. Rozell, Don. H. Johnson and Raymon M. Glantz Department of Electrical & Computer Engineering Department of
Dynamic Outlier Algorithm Selection for Quality Improvement and Test Program Optimization
 Dynamic Outlier Algorithm Selection for Quality Improvement and Test Program Optimization Authors: Paul Buxton Paul Tabor 5/21/04 Purpose Outliers and quality improvement Outliers and test program optimization
Dynamic Outlier Algorithm Selection for Quality Improvement and Test Program Optimization Authors: Paul Buxton Paul Tabor 5/21/04 Purpose Outliers and quality improvement Outliers and test program optimization
STAT 200. Guided Exercise 4
 STAT 200 Guided Exercise 4 1. Let s Revisit this Problem. Fill in the table again. Diagnostic tests are not infallible. We often express a fale positive and a false negative with any test. There are further
STAT 200 Guided Exercise 4 1. Let s Revisit this Problem. Fill in the table again. Diagnostic tests are not infallible. We often express a fale positive and a false negative with any test. There are further
Analysis and Interpretation of Data Part 1
 Analysis and Interpretation of Data Part 1 DATA ANALYSIS: PRELIMINARY STEPS 1. Editing Field Edit Completeness Legibility Comprehensibility Consistency Uniformity Central Office Edit 2. Coding Specifying
Analysis and Interpretation of Data Part 1 DATA ANALYSIS: PRELIMINARY STEPS 1. Editing Field Edit Completeness Legibility Comprehensibility Consistency Uniformity Central Office Edit 2. Coding Specifying
The Z Test. Assignment. Terms You Should Know. Psychological Statistics The Z Test. G&W, Chapter 6. Z-test
 Assignment G&W, Chapter 6 Terms You Should Know. Z-test Critical Value of Z when p
Assignment G&W, Chapter 6 Terms You Should Know. Z-test Critical Value of Z when p
Applied Statistical Analysis EDUC 6050 Week 4
 Applied Statistical Analysis EDUC 6050 Week 4 Finding clarity using data Today 1. Hypothesis Testing with Z Scores (continued) 2. Chapters 6 and 7 in Book 2 Review! = $ & '! = $ & ' * ) 1. Which formula
Applied Statistical Analysis EDUC 6050 Week 4 Finding clarity using data Today 1. Hypothesis Testing with Z Scores (continued) 2. Chapters 6 and 7 in Book 2 Review! = $ & '! = $ & ' * ) 1. Which formula
Behavioral Data Mining. Lecture 4 Measurement
 Behavioral Data Mining Lecture 4 Measurement Outline Hypothesis testing Parametric statistical tests Non-parametric tests Precision-Recall plots ROC plots Hardware update Icluster machines are ready for
Behavioral Data Mining Lecture 4 Measurement Outline Hypothesis testing Parametric statistical tests Non-parametric tests Precision-Recall plots ROC plots Hardware update Icluster machines are ready for
MOST: detecting cancer differential gene expression
 Biostatistics (2008), 9, 3, pp. 411 418 doi:10.1093/biostatistics/kxm042 Advance Access publication on November 29, 2007 MOST: detecting cancer differential gene expression HENG LIAN Division of Mathematical
Biostatistics (2008), 9, 3, pp. 411 418 doi:10.1093/biostatistics/kxm042 Advance Access publication on November 29, 2007 MOST: detecting cancer differential gene expression HENG LIAN Division of Mathematical
Outlier detection in datasets with mixed-attributes
 Vrije Universiteit Amsterdam Thesis Outlier detection in datasets with mixed-attributes Author: Milou Meltzer Supervisor: Johan ten Houten Evert Haasdijk A thesis submitted in fulfilment of the requirements
Vrije Universiteit Amsterdam Thesis Outlier detection in datasets with mixed-attributes Author: Milou Meltzer Supervisor: Johan ten Houten Evert Haasdijk A thesis submitted in fulfilment of the requirements
Chapter 23. Inference About Means. Copyright 2010 Pearson Education, Inc.
 Chapter 23 Inference About Means Copyright 2010 Pearson Education, Inc. Getting Started Now that we know how to create confidence intervals and test hypotheses about proportions, it d be nice to be able
Chapter 23 Inference About Means Copyright 2010 Pearson Education, Inc. Getting Started Now that we know how to create confidence intervals and test hypotheses about proportions, it d be nice to be able
Social Determinants of Health
 FORECAST HEALTH WHITE PAPER SERIES Social Determinants of Health And Predictive Modeling SOHAYLA PRUITT Director Product Management Health systems must devise new ways to adapt to an aggressively changing
FORECAST HEALTH WHITE PAPER SERIES Social Determinants of Health And Predictive Modeling SOHAYLA PRUITT Director Product Management Health systems must devise new ways to adapt to an aggressively changing
Automated Assessment of Diabetic Retinal Image Quality Based on Blood Vessel Detection
 Y.-H. Wen, A. Bainbridge-Smith, A. B. Morris, Automated Assessment of Diabetic Retinal Image Quality Based on Blood Vessel Detection, Proceedings of Image and Vision Computing New Zealand 2007, pp. 132
Y.-H. Wen, A. Bainbridge-Smith, A. B. Morris, Automated Assessment of Diabetic Retinal Image Quality Based on Blood Vessel Detection, Proceedings of Image and Vision Computing New Zealand 2007, pp. 132
Previously, when making inferences about the population mean,, we were assuming the following simple conditions:
 Chapter 17 Inference about a Population Mean Conditions for inference Previously, when making inferences about the population mean,, we were assuming the following simple conditions: (1) Our data (observations)
Chapter 17 Inference about a Population Mean Conditions for inference Previously, when making inferences about the population mean,, we were assuming the following simple conditions: (1) Our data (observations)
EECS 433 Statistical Pattern Recognition
 EECS 433 Statistical Pattern Recognition Ying Wu Electrical Engineering and Computer Science Northwestern University Evanston, IL 60208 http://www.eecs.northwestern.edu/~yingwu 1 / 19 Outline What is Pattern
EECS 433 Statistical Pattern Recognition Ying Wu Electrical Engineering and Computer Science Northwestern University Evanston, IL 60208 http://www.eecs.northwestern.edu/~yingwu 1 / 19 Outline What is Pattern
4. Model evaluation & selection
 Foundations of Machine Learning CentraleSupélec Fall 2017 4. Model evaluation & selection Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech chloe-agathe.azencott@mines-paristech.fr
Foundations of Machine Learning CentraleSupélec Fall 2017 4. Model evaluation & selection Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech chloe-agathe.azencott@mines-paristech.fr
Classification of Synapses Using Spatial Protein Data
 Classification of Synapses Using Spatial Protein Data Jenny Chen and Micol Marchetti-Bowick CS229 Final Project December 11, 2009 1 MOTIVATION Many human neurological and cognitive disorders are caused
Classification of Synapses Using Spatial Protein Data Jenny Chen and Micol Marchetti-Bowick CS229 Final Project December 11, 2009 1 MOTIVATION Many human neurological and cognitive disorders are caused
Abstract. Optimization strategy of Copy Number Variant calling using Multiplicom solutions APPLICATION NOTE. Introduction
 Optimization strategy of Copy Number Variant calling using Multiplicom solutions Michael Vyverman, PhD; Laura Standaert, PhD and Wouter Bossuyt, PhD Abstract Copy number variations (CNVs) represent a significant
Optimization strategy of Copy Number Variant calling using Multiplicom solutions Michael Vyverman, PhD; Laura Standaert, PhD and Wouter Bossuyt, PhD Abstract Copy number variations (CNVs) represent a significant
Classification of ECG Data for Predictive Analysis to Assist in Medical Decisions.
 48 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.10, October 2015 Classification of ECG Data for Predictive Analysis to Assist in Medical Decisions. A. R. Chitupe S.
48 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.10, October 2015 Classification of ECG Data for Predictive Analysis to Assist in Medical Decisions. A. R. Chitupe S.
WDHS Curriculum Map Probability and Statistics. What is Statistics and how does it relate to you?
 WDHS Curriculum Map Probability and Statistics Time Interval/ Unit 1: Introduction to Statistics 1.1-1.3 2 weeks S-IC-1: Understand statistics as a process for making inferences about population parameters
WDHS Curriculum Map Probability and Statistics Time Interval/ Unit 1: Introduction to Statistics 1.1-1.3 2 weeks S-IC-1: Understand statistics as a process for making inferences about population parameters
Data visualisation: funnel plots and maps for small-area cancer survival
 Cancer Outcomes Conference 2013 Brighton, 12 June 2013 Data visualisation: funnel plots and maps for small-area cancer survival Manuela Quaresma Improving health worldwide www.lshtm.ac.uk Background Describing
Cancer Outcomes Conference 2013 Brighton, 12 June 2013 Data visualisation: funnel plots and maps for small-area cancer survival Manuela Quaresma Improving health worldwide www.lshtm.ac.uk Background Describing
Data mining for Obstructive Sleep Apnea Detection. 18 October 2017 Konstantinos Nikolaidis
 Data mining for Obstructive Sleep Apnea Detection 18 October 2017 Konstantinos Nikolaidis Introduction: What is Obstructive Sleep Apnea? Obstructive Sleep Apnea (OSA) is a relatively common sleep disorder
Data mining for Obstructive Sleep Apnea Detection 18 October 2017 Konstantinos Nikolaidis Introduction: What is Obstructive Sleep Apnea? Obstructive Sleep Apnea (OSA) is a relatively common sleep disorder
